Critical Decisions for Critical Infrastructure: How Best to Implement Precise Time and Synchronization
August 23, 2021
Story
Critical infrastructure services such as telecommunications, utilities, transportation, and defense require Positioning, Navigation, and Timing (PNT) technology to operate. But the ubiquitous use of the Global Positioning System (GPS) as the primary source of PNT information has introduced vulnerabilities.
In early 2020, Executive Order (E.O.) 13905 on Strengthening National Resilience through Responsible Use of PNT Services was signed to strengthen, through policy promotion, the responsible use of PNT services by government and infrastructure operators.
Operators must make two most critical decisions as they create a PNT solution for their critical infrastructure: 1) Should resiliency, redundancy, and security be deployed at every layer of the architecture?; and 2) What security strategy should be used?
Decision #1: Every Layer?
Operators worry, with good reason, that they cannot justify the costs associated with deploying resiliency, redundancy, and security at every layer of the architecture. There are new timing and synchronization solutions and design options that enable the optimal cost structures for robust and reliable solutions.
Tradeoffs between cost and solution type are generally related to the location where they will be deployed. With the migration from SDH/TDM to Ethernet and the development of LTE/4G and 5G in mobile, there are significantly more aggregation offices and network access sites at the edge. This has inevitably led to smaller, typically 1-U rack-mountable devices whose costs are in line with today’s much smaller edge base stations, including small cells and gNodeBs. In this environment, operators must decide how to provide redundancy, resiliency, and security at the architecture level and the design level.
Redundancy can be engineered at the architecture level with core functions at both ends of an east/west deployment. As an example, the virtual Primary Time Reference clock (vPRTC) architecture delivers directional redundancy and high-performance capabilities through dual paths. It also offers cost-effective distribution through efficient high-accuracy time transfer over the long haul.
Another way to deploy redundancy is in the device itself. The best approach is software redundancy, which enables a low-cost, efficient, and high-performance distributed solution. It avoids the cost of a hardware module that also consumes space, typically for input and output ports, and eliminates having to trade other valuable capabilities for the benefits of adding redundancy. For example, there are tradeoffs and potential compromises when choosing between 10 Giga Ethernet (GE) support and multiband Global Navigation Satellite System (GNSS) if redundancy is enabled. In contrast, software redundancy does not require removing any hardware and forfeiting the associated function.
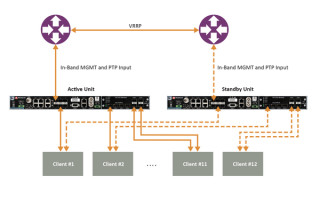
Figure 1 shows a common redundancy use case with two aggregation routers using virtual router redundancy protocol (VRRP).

Figure 1: Example of redundancy connectivity between the active and standby units.
The other advantage of software redundancy is it enables total redundancy of the entire device. The active and standby units are the same. Every capability is redundant, including oscillator, GNSS receiver, ports, and input/outputs. With a hardware module, it is only redundant for its own features, not the rest of the unit.
Like redundancy, resiliency is also deployed at both the architecture and device level. It is deployed at the architecture level so that the network’s grandmasters can be connected to each other. When grandmasters are connected to GNSS as their source of time and frequency, they must be connected to other 1588 grandmasters to enable Assisted Partial Time Support (APTS). In case of a GNSS failure at the grandmaster location, APTS facilitates backup by enabling the use of Automatic Asymmetry Correction (AAC) to calibrate the different paths a PTP flow may use to/from upstream grandmasters. A backup path to an upstream grandmaster can guarantee uninterrupted and precise time and phase operation. This architecture ensures GNSS can be backed up by IEEE 1588 Precise Time Protocol (PTP) when interrupted, using the best path.
vPRTC offers an alternative. It enables operators to employ a chain of high-performance boundary clocks using PTP over long distances for high accuracy, typically over optical networks. This architecture uses PTP as its primary source of time and phase, reducing reliance on GNSS.
At the device level, resiliency is implemented through the optimal choice of an oscillator (from OCXO to a Rubidium atomic clock). The selection is based on location, use case, and timekeeping holdover performance requirements. It is vital to specify a multi-band GNSS receiver. Only these receivers can gauge and mitigate significant time delays during cyclical ionospheric events such as solar storms, by using the delay differences in time information that GNSS satellites transmit across several frequency bands. This is critical for applications requiring Primary Reference Time Clock class B (PRTC-B) 40ns as well as enhanced PRTC (ePRTC) 30ns.
Decision #2: What Security Strategy?
The best security approach is to start with a standard framework and consider other vulnerabilities including evolving jamming and spoofing threats.
Authentication and authorization options based on a standard framework include Terminal Access Controller Access Control System + (TACACS+) and Remote Authentication Dial-In User Service (RADIUS). Two-factor authentication (2FA) provides an extra layer of protection beyond the security provided by a username and password.
Providing Secure Shell (SSH) extensions with various levels of security profiles increases granularity for determining which types of users have what levels of access rights and limitations. High-security profiles will ensure the most stringent access rules can be defined and enforced. It is also necessary to address scripting vulnerabilities as well as relevant Common Vulnerabilities and Exposures (CVE®). This ensures all potential security holes are being reviewed and addressed. To combat evolving jamming and spoofing threats, signal monitoring must be implemented along with consistency checks and remediation.
Making the right architecture choices to ensure continued performance requires a thorough network engineering study. It must include a careful analysis of grandmaster deployment locations and how much performance and accuracy they will need to provide. This evaluation will guide the selection process for precise time and synchronization devices. Network planners and synchronization engineers should also consider choices such as fan less devices or those that require a fan, the cost and other implications of implementing redundancy though modular hardware or software, and whether to use embedded or modular GNSS. Armed with the right information and a thorough understanding of their options, critical infrastructure operators can cost-effectively deploy the necessary redundancy, resiliency, and security to create a robust and reliable PNT solution.
More information about architecture choices and solutions is available at t vPRTC. White papers on this and other topics can be downloaded at this this link.