Revisiting the CAN bus to secure connected cars
June 13, 2017
Story
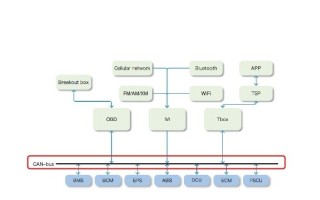
The CAN bus and its security are at the center-stage after a number of high-profile hacking events that shook the automotive industry during the past couple of years. The intra-vehicle data...
The CAN bus and its security are at the center-stage after a number of high-profile hacking events that shook the automotive industry during the past couple of years. The intra-vehicle data channel between control units like airbags and ECUs has become the most common entry point for car hackers. The CAN bus access, for instance, is readily available via the OBD port otherwise used to retrieve vehicle data at service stations. That’s because the Internet of Cars wasn’t exactly a design consideration during the last decade or before that when engineers began deploying CAN bus to allow different parts of the vehicle to communicate with each other.
Then came the rude awakening during the mid-2010s when hackers like Charlie Miller openly demonstrated the vulnerabilities of vehicle onboard computers and networks like CAN bus linking these onboard computers. Now the industry is quickly recognizing the need for the secure networks for safe communications between ECUs.
[The CAN bus is at the heart of connected car security.]
CAN bus is a hardware-plus-software protocol, so both hardware and software solutions are emerging to prevent security breaches happening because of compromises in network-enabled onboard computers via CAN bus access. Take Mercury Systems, which has unveiled the CANGuard software solution that denies malicious intrusion attempts on vehicle onboard computers and networks. The security suite — installed in the ECU attached to a vehicle’s CAN bus — blocks malicious data traffic before it can have an impact on the vehicle. And unlike other software solutions, such as CAN bus firewalls and traffic monitoring, CANGuard doesn’t require any architectural changes or additional hardware.
On the hardware front, the in-car controllers are increasingly integrating security features to raise the bar on protections against malicious attacks. For instance, STMicro’s SPC56 family of automotive microcontrollers combines Ethernet and CAN FD communication interfaces with the hardware security module (HSM) technology to secure the ECU links. Next, ST’s Telemaco3 automotive processors boast a secure CAN subsystem to deny attacks on vehicle’s drive-train, chassis, and safety systems connected to the CAN bus. The security mechanism relies on the ARM Cortex-M3 core, which manages the interface with the CAN network and is segregated from the main system that runs on a dual Cortex-A7.
These developments clearly show that the automotive industry is finally coming to terms with the darker side of the connected car movement. Especially when the number of connected vehicles is rapidly expanding, carmakers simply can’t afford to leave the CAN bus unprotected.





