Making Smart Cities More Secure
July 12, 2022
Story

Smart cities are on the march again. If anything, the experience of the pandemic has strengthened the resolve of urban planners to design and build safer, more efficient, and healthier living environments.
Now the market is set to be worth over $2 trillion by 2026. But the rush to digitalize shouldn’t be undertaken without managing the inherent risks involved in rolling out large scale IoT projects.
Security-by-design principles should be front-of-mind throughout, which means starting with an underlying network ecosystem with certificate-based device authentication and strong encryption at its heart.
Dangers of the Smart City
The rapid growth in IoT devices worldwide has not gone unnoticed. There has been a similar surge in cyber-threats targeting these systems. From 2019 to 2020, Nokia observed a 100% growth in IoT device infection rates. Such devices now account for a third (32%) of all infected devices, according to the network specialist. It also warns that IoT botnets account for a third of all malware incidents detected by its endpoint security product.
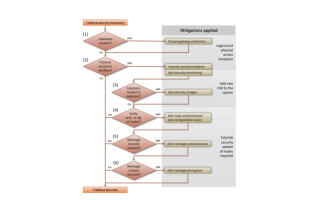
In a smart city environment, there are several risks. If devices and networks cannot be authenticated and messages encrypted, there are opportunities for threat actors to spoof, steal, modify, or destroy data in transit as well as disrupt access to the network. In practice, this could enable attackers to sabotage smart city projects, hold them to ransom, and/or make off with sensitive data.
The challenge is that IoT devices are often constrained by limited resources and energy, and may be physically accessible for tampering. Wireless networks are also easily “overheard” and therefore can be difficult to physically protect.
The Importance of Certificate-Based Authentication
In this context, it’s vital that each device can be uniquely identified and authenticated when joining a network, and indeed that the network can be certified as legitimate—in order to mitigate the risk of spoof networks designed to hijack devices and data flows. Passwords and shared secrets have been proven to fail at security and/or scalability.
The best way to authenticate devices is therefore via certificate-based authentication with TLS. It means both IoT devices and the cloud systems they connect to have identities which can be used to establish trust, and use private, encrypted communications. Devices and clouds present certificates to each other issued by a mutually trusted authority (CA). During a handshake, entities present their identity certificate, and the receiving party can verify that identity certificate chains up to a root of trust.
The world standard for this device identity, used by Wi-SUN, is the X.509 public key certificate, an electronic document based on an ISO/IEC/ITU-T standard which contains information about its owner, operator, or manufacturer and binds this to a unique public cryptography key. This ensures secrets always stay secret and the document cannot be modified.
This is all underpinned by Public Key Infrastructure (PKI), a tried-and-tested framework of encryption standards which has been securing data comms over public networks for decades. It enables a range of security principles essential to any IoT ecosystem, including: authentication of entities; encryption of data at rest and in motion; data integrity, to ensure no tampering in transit; and authorization. It’s also scalable to hundreds of millions of entities per ecosystem—perfect for smart cities—and interoperable with a wide range of software and services.
Building Up the Layers
Device identity and certificate-based authentication is a great foundation for smart city security. But there are more elements which can further mitigate risk.
They include device hardening with 802.1AR and a Hardware Secure Element — a chip designed to protect against unauthorized access — or a Physical Unclonable Function (PUF). The latter is akin to a “fingerprint” derived from the unique characteristics of a piece of silicon which can be turned into a unique cryptographic key and used as the chip’s root key. No additional hardware is needed to store the key securely, and it becomes invisible to attackers when a device is powered off.
Another benefit that comes from using certificates is the inclusion of “firmware signing”. This allows a device to verify the integrity of its software program, proving that the code in the device has not been tampered with.
Other security features deployed by Wi-SUN include over-the-air upgradable devices to ensure endpoints are hardened from potential exploitation, and frequency hopping—an FCC requirement which prevents attackers from jamming signals which could deny service.
We also support role-based access controls, 802.1x-based access control for meters, routers and grid devices, and IEEE 802.15.4 link-layer encryption for RF mesh networks. This comes alongside internationally recognized standards for network authentication (IETF EAP-TLS) and key management (IEEE 802.11i). It’s hard to understate the importance of following standards in IoT security architectures. They denote quality, reliability, and optimized security. As well as accelerating time-to-market and lowering development costs, standards-based systems denote interoperability, and freedom from vendor lock-in.
Read Phil's next blog, Why Open Standards are the Key to Building Smarter Cities and Grids.
Phil Beecher is the president and CEO of Wi-SUN Alliance, a global non-profit member-based association driving the proliferation of interoperable wireless solutions for use in smart cities and other IoT applications. He can be reached at [email protected]