Things you Might Not Know about the IoT Security Life Cycle
September 21, 2018
Blog

Problems revolve around protecting IoT devices and scaling the security across millions and billions of devices encompasses far more than encryption and device security.
Mocana recently announced a partnership with Verizon and their ThingSpace platform which, at first glance, seems to be an announcement around an increased level of security capabilities as part of Verizon’s 5G/IoT initiatives. But looking deeper into Mocana, their approach and solution sets, this is more about an effective security lifecycle than a simple “keep things secure” solution.
Mocana History
Mocana was founded in 2002 as an embedded security software company for military embedded systems including avionics controllers on military aircraft, tanks, ships and drones. These systems need to be tamper proof, and, while not necessarily being connected to the internet, there are significant concerns around physical access and data protection. Early on, Mocana provided cryptographic tools and software to handle authentication, encryption, and device and data integrity in a footprint that would fit in a microcontroller. Over the past 16 years this has expanded protecting over 100 million devices in industries that range from military and industrial to oil/gas, medical and transportation.
From Products to Lifecycle
Keao Caindec, vice president of marketing with Mocana, mentioned these baseline capabilities had broad appeal to embedded systems and IoT. But with billions of devices, the problems revolve around protecting connected devices and scaling the security across millions and billions of devices encompasses far more than encryption and device security. This means adhering to a complete security lifecycle. There are significant security challenges at each stage of an IoT product - design, development, manufacturing, activation, management, maintenance, and even end-of-life. Mocana began developing solutions around the security lifecycle of IoT and has never looked back.
IoT Endpoint Security During Development
Usually the security software to protect the IoT endpoints is integrated with the application software on those endpoints. The security software is often in the firmware of the microcontroller. Mocana offers TrustPoint™, which includes a development framework, binaries, source code, and application programming interfaces to protect an IoT device throughout the lifecycle. TrustPoint helps address security challenges during the development cycle by providing software that can be integrated into the application during development. The APIs and functionality of the software makes developers more “security aware” during development.
Mocana TrustPoint integrates with over 70 chipsets from ARM/Intel to NXP, Xilinx, ST Micro, Atmel, Infineon, and others. It also integrates with crypto accelerators and device security elements. “Integrating embedded security technologies is complex. Software developers may need to integrate a hardware secure element like a TPM and offload crypto functions to a crypto accelerator. They may also need secure multiple stages of the boot process. Unless you are an experienced cryptopgrapher, it is challenging to integrate security into devices without inadvertently creating more vulnerabilities,” Keao said.
Addressing the Security Lifecycle Past the Development
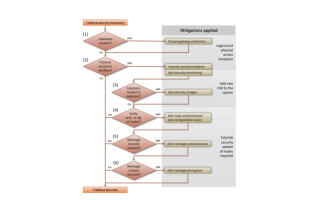
Baking the security hooks into the IoT endpoints doesn’t ensure security. Mocana also has a product called TrustCenter™ that is a platform for managing the security lifecycle. There are a number of steps involved and each one must be addressed in order to minimize vulnerabilities.
Time for a quiz – Keao pointed out six post-installation stages of an IoT lifecycle that are often overlooked. If you want to play along, don’t look down, get a pen or pencil, and write down post installation IoT lifecycle stages that involve security, then read on – how many did you get?
- Device Enrollment. Once the device is manufactured, installed, and turned on, there is an enrollment step. This may involve putting some kind of unique identifier on the device like a MAC address or unique user ID (UUID). Enrollment involves loading the secure credential or certificate that can be used to support the cryptographic functions. This process giving a device a unique ID tends to be manual today and may involve using a JTAG-to-USB connector for manual insertion or perhaps implementing this over a radio or modem. Once the IDs are on the device, you enroll it. The enrollment process can be insecure with no attestation – no way to ensure the device is really the device you think it is. Methods like using a simple ID/password to access a domain request for getting a digital certificate is rather weak and can be prone to compromise. Mocana’s TrustCenter automates the enrollment process to close the system to minimize manual intervention and the circle of knowledge for enrollment while enabling device enrollment to scale to millions or billions of devices.
- Operation. Many cyber attacks attempt to expose unprotected ports that have little or no authentication. As long as you have port access and a network address, access is possible. Once access is achieved the attacker can leverage an admin console or CLI to disrupt operation depending on what kind of access the software being controlled has. Mocana TrustPoint enables devices to use strong authentication using PKI or extended authentication protocols like EAP and RADIUS to ensure that only authorized devices can communicate with each other using device-to-device authentication in addition to passwords and port access.
- Updates. Many software attacks expose vulnerabilities during the software update process. Being able to mimic software update notifications or responses allows the attacker to update the firmware with malware. The malware may be a worm or Trojan that takes control of the device and sends private data elsewhere or launches other attachments. Mocana addresses this by providing software update tools with strong authentication to access the device, then encrypting the software update image so that only a trusted device can decrypt it. Ensuring only trusted parties can connect is an additional safeguard, but one that isn’t necessarily an option depending on the IoT application.
- Administration/maintenance. Errors can occur during the administration and maintenance lifecycle stages. For this purpose, Mocana TrustCenter uses multi-factor verification with PKCS 7 standards to secure the update process. This allows multiple parties to sign for authentication. This is a powerful and often overlooked aspect where if you get the device manufacturer, software developer, and system admin to all sign, the chances of failure or errors due to overlooking one aspect is minimized.
- Ownership Transfer. What happens when you need to transfer ownership of IoT endpoints? How do you securely remove certs, transfer to the next owner, ensure on-device data is wiped out reliably without fear of compromise or data access? Mocana TrustCenter enables administrators to handle this using standards-based protocols and methods.
- End-of-Life. How do you retire devices securely? IoT is so new, this is something that is likely to be overlooked, but not by Mocana. If you’re removing an endpoint, it’s not as simple as just un-installing it and you’re done. Similar to the ownership transfer, retired endpoint certificates and credentials must be properly removed system-wide and the device may need to have memory wiped to avoid data exposure.
How many did you get? Did you identify any stages that aren’t above? Let me know – I’m interested in scenarios you feel are security vulnerabilities not mentioned here.
Mocana TrustCenter deals with security deficiencies in the IoT life cycle. TrustPoint deals with removing complexity involved with integrating security on IoT devices. Having gone through these in more detail, it becomes apparent how significant this announcement really is.
This partnership embraces the end-to-end security issues involved with IoT and the challenges users of Verizon Thingspace face when deploying IoT solutions on the Verizon platform. The partnership solves unique challenges involved with the entire lifecycle of an IoT system. And by association, it minimizes security issues on the Verizon network.
Keao summed it up best when he addressed attempts to apply enterprise data center security solutions to an IoT system. “The biggest problem is an over-reliance on network and IT security approaches to protect IoT systems. The IoT environment lives outside the walls of a datacenter or enterprise firewall perimeter. Enterprise security doesn’t solve IoT security challenges. IoT security has to be addressed from the hardware up. The industry needs to standardize on ways to address the many new attack vectors of IoT we didn’t see when these IT security standards were written over a decade ago.”